AWS Web Application Firewall or WAF for short is an important service for any application that hosts publicly facing APIs.
In this article, I’m going to briefly explain to you what WAF is all about including why it’s important and the key features you need to know about when using WAF.
So let’s start with an example to understand where AWS WAF fits in and why its important.
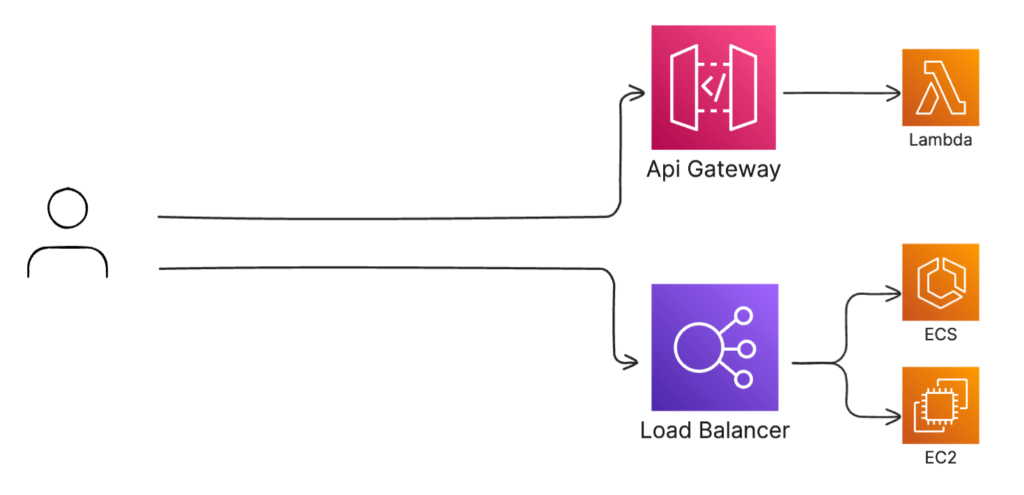
In the screenshot below are two common ways to build APIs. The top one is with an API gateway backed by a Lambda function, and the bottom one is with a load balancer fronting traffic for ECS or EC2.
In a perfect world, we would only need to worry about users calling our APIs in an expected way. But today, there a lot of bad actors that can threaten our system and our pocketbooks. Some of these threats include:
- DDoS or distributed Denial of Service attacks which flood your endpoints with server traffic to prevent legitimate users from accessing your application.
- SQL injection which attempts to embed malicious query statements that can expose access to your data.
- XSS or Cross Site Scripting attacks which attempt to inject malicious snippets of code into your APIs to gain control of your system.
- And finally, since AWS uses a pay per use model, a large influx of requests have a potential to consume resources and result in an unexpected bill.
These are just a couple of examples of some popular threats but there are many more.
AWS WAF sits in front of your API endpoints to act as a first layer of defence. It’s a service that enhances application security by examining incoming traffic and rejecting it if it matches a certain pattern. You can use it to prevent SQL injection, XSS, ban certain IPs or CIDR blocks, and a whole lot more. It even supports rate limiting to prevent abuse by clients.
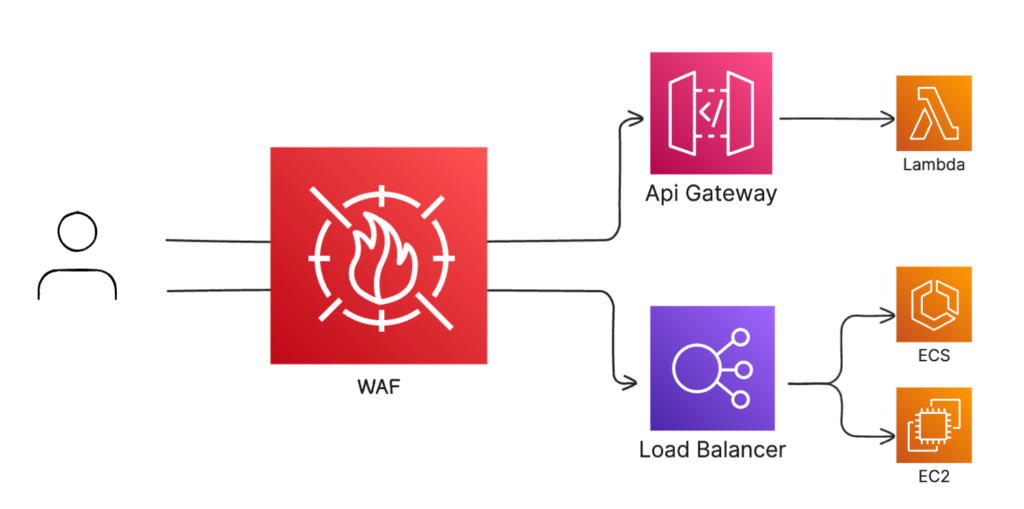
You can use WAF to protect many of your publicly facing resources. The list of supported services include:
- Cloudfront
- API Gateway
- Application Load Balancers
- Cognito User Pools
- AppSync
- App Runner
You can easily add WAF in front of one or more of these services with a single configuration.
Before we can get into the console showing you how to set up WAF, lets quickly touch on three important concepts you need to know about: 1) Web Access Control Lists, 2) Rules, and 3) Rule Groups.
Web ACLs
Web ACLs are the top level entities that are applied to resources that you would like to protect. Web ACLs have a dashboard that show you how much traffic is being allowed or blocked based on the its configuration.
Rules
Within Web ACLs, you can create Rules. Rules define how to inspect incoming requests and the actions to take if the request matches the inspection criteria. For example, you can configure a rule to look for SQL Injection within the request, look for a specific or group of IP addresses, or look for traffic from a certain origin country. You can apply just a single rule, or create multiple and join them together with logical operators like AND or OR.
As part of your rule, you can inspect different parts of the request such as query parameters, the request headers, or the request body.
When traffic matches a rule, you define the action that you would like to take. This includes:
- Allow to let the requestthrough to the resource
- Block to deny the request
- Captcha to challenge the user with a puzzle to solve
- Count which simply counts the number of requests that match the pattern. Counting is useful for testing a rule before you apply it.
Keep in mind that rules are not an actual entity in AWS WAF. This means that they don’t have any ID or Amazon Resource Name, AND you wont be able to find them anywhere in the console under any “Rules” section. They strictly exist as a JSON object that you define to be used for your ACL.
Rule Groups
There are two ways to create rules, either directly within the Web ACL, or as part of a Rule Group. Rule groups are collections of rules that you can apply to multiple different Web ACLs. So for example, if have a set of rules that are specific to your company, you can create a Rule Group and apply them to multiple different Web ACLs.
You can also choose to buy pre-created rule groups from the AWS Marketplace. These Rule Groups are created by AWS partners and protect your resources from a variety of threats. Keep in mind though to use groups created by partners, additional fees will apply.
So this is a broad overview of AWS Web Application Firewall. To learn more about WAF and how to use it to protect your application, check out the AWS developer guide here.







